Network Discovery, Inventory And Audit: Open-AudIT
See exactly what is on your network, how it is configured, and when it changes. 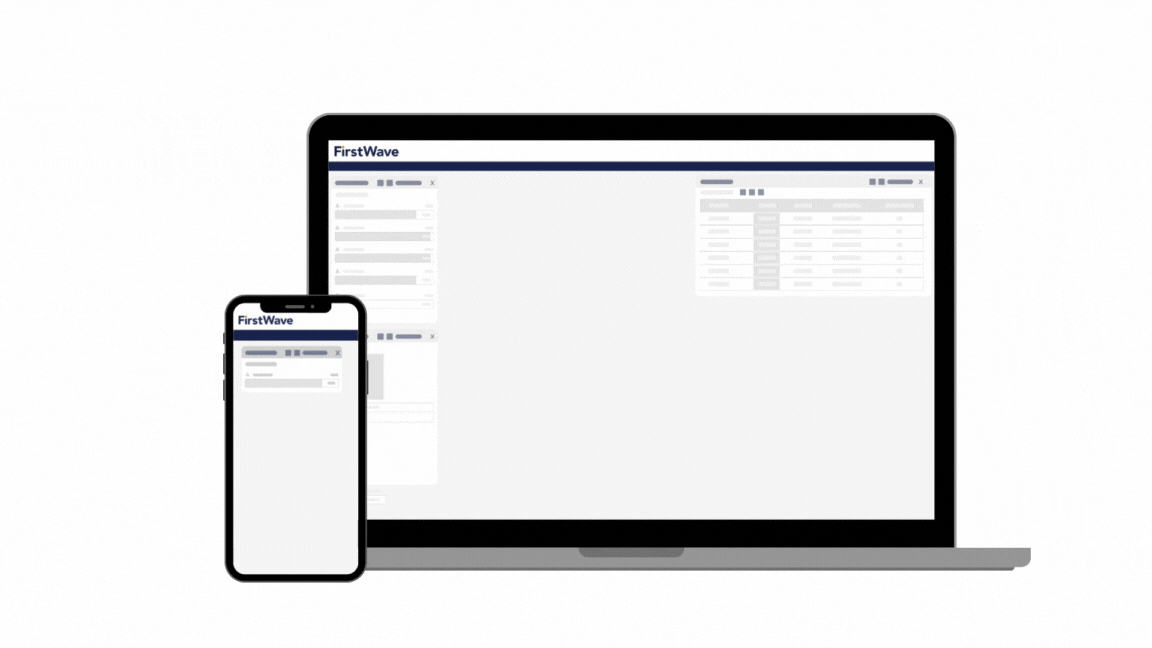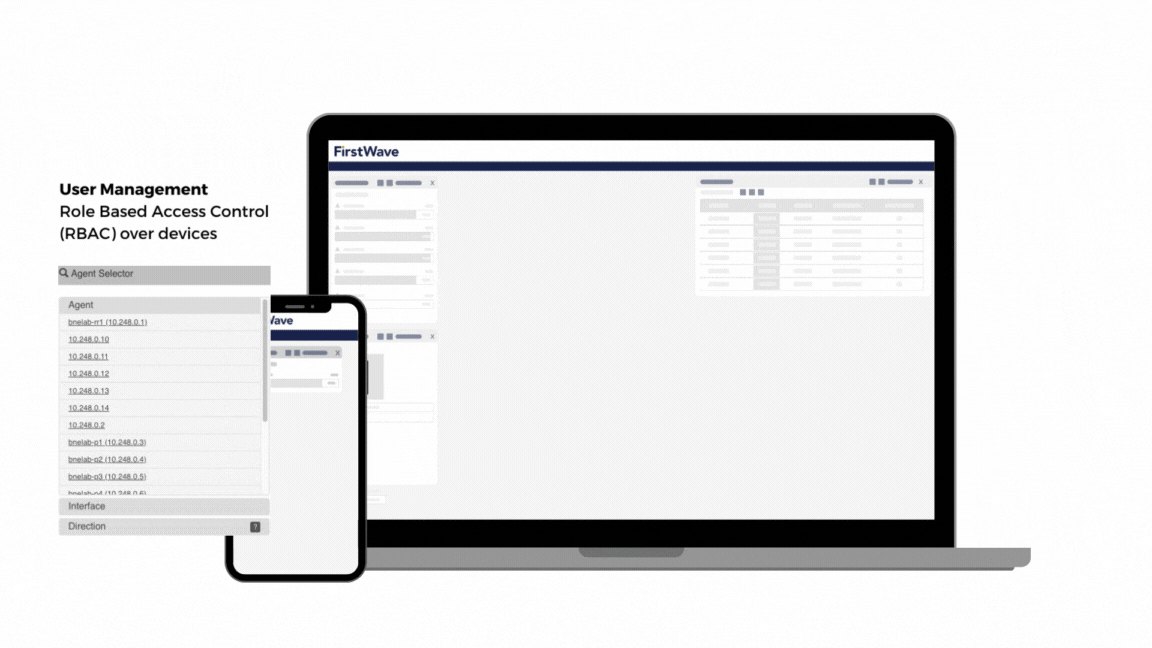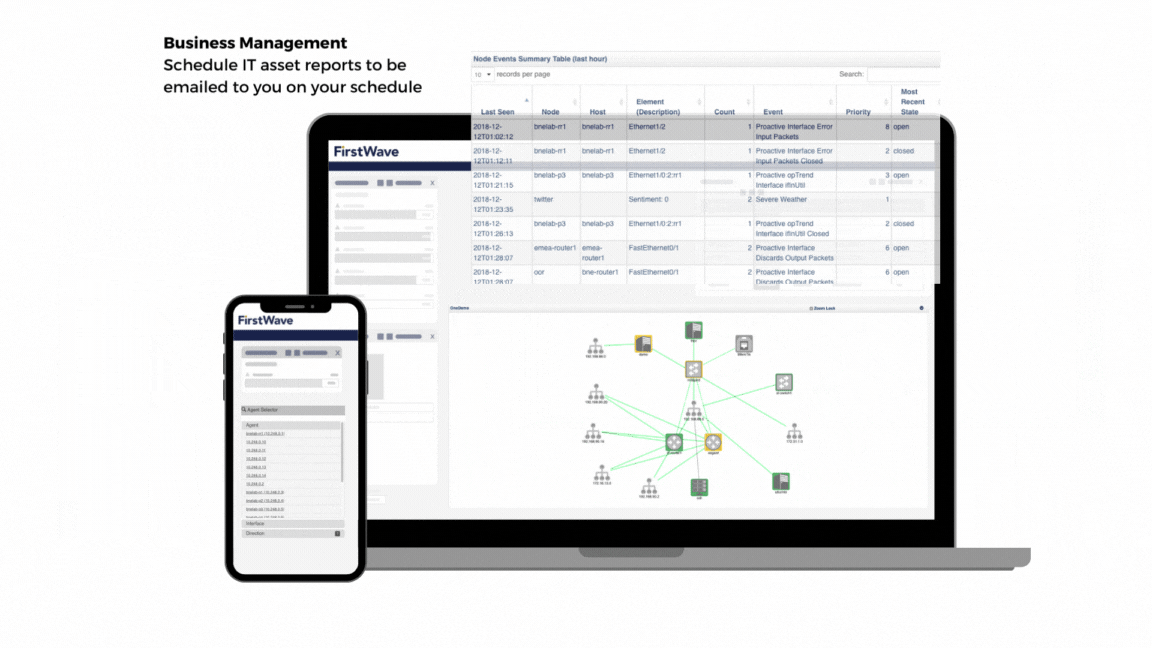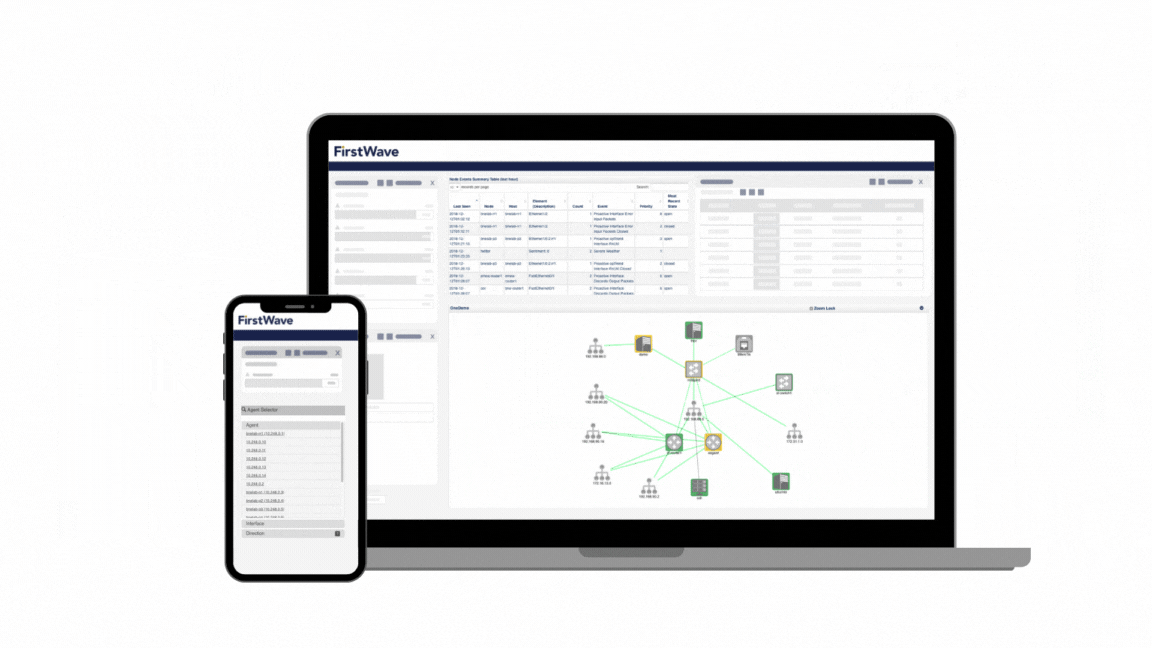
Open-AudIT is an application to tell you exactly what is on your network, how it is configured and when it changes. Most organizations cannot give accurate location data of their assets, Open-AudIT gives you this information in seconds.
Open-AudIT intelligently scans an organization’s network and stores the configurations of the discovered devices. This gives you immediate access to software licensing, configuration changes, non-authorized devices, capacity utilization and hardware warranty status reports. Open-AudIT can collect significant amounts of data from large and varying networks that are cataloged and can easily be configured into meaningful reports.
It’s no wonder why Open-AudIT is used by over 130,000 organizations worldwide.
Open-AudIT Benefits
Automate Your Network Discovery, Reporting, and Control
Easily create network discovery profiles and then run a discovery with a single click or even automated.
Track and report IT asset configuration changes and software licensing, shadow IT, and hardware warranty status.
The scheduler will give you the results by email, JSON, CSV, XML, or HTML.
Open-AudIT’s user roles have a set of permissions (Create, Read, Update, Delete) for each endpoint. Roles can also be used with LDAP (Active Directory and OpenLDAP) authorization.
The compliance system compares software, hardware, users and netstat data against your required standard.
Get definitive lists of all of your software licensing alongside your asset management. Get historical snapshots for easy comparison.
Download Data Sheet
Find out how FirstWave’s Open-AudIT can help you see exactly what’s on your network?
Free Download Book A Call
Open-AudIT Features
High-Power Out-of-the Box Features For Intelligent Network Management

Custom Notifications
- Email reports can be filtered by the organization, sending only relevant data
- Emails can be to one or more contacts
- Reports/lists can be in CSV, JSON, HTML and XML formats Email scheduling of any report

Business Services
- Open-AudIT tracks every device on your network, it will record changes, additions or removals
- Schedule discoveries to ensure all devices are kept up to date
- Full lists of software, services, disks, open ports and users are monitored for additions, changes and removals
- Schedule IT asset reports to be emailed to you on your schedule, stay ahead of auditors

User Management
- Role Based Access Control (RBAC) over devices
- Custom business hours rules

Easy Implementation
- Easy installation
- Dependencies are installed automatically
- CSV import and script ready
Support available for installation and customization
Accessibility
- Extensive Role-Based Access control mechanisms
- Accessible from any device
- Single Sign On across all our applications
- RESTful JSON API & standard CRUD functionality

Powerful Interface
- The Open-AudIT home dashboard is ready to go with information
- Run discoveries/audits on demand or look at historical reports
- Accessible from any common browser

Flexible Licensing
- Open-AudIT is licensed by the device count
- There are no limits on the number of discoveries or audits
- Subscription licensing available
Infinitely scalable architecture

Pricing and Purchasing
- Licensed by the device and not by the quantity of discoveries/ audits
- Fixed license costs
- MSP Scale licensing available
- Unlimited user accounts

Sales and Support
- Easy to purchase – trial it yourself for free or contact us for a demo
- Support portal access
- Complete documentation and support wiki available
- Pay as you grow options are available
- Free updates
Open-AudIT Features Comparison Chart
License Tier Inclusions
Open-AudIT Enterprise discovers every device on your network. Discoveries are at the very heart of what Open-AudIT does. How else would you know “What is on my network?”
Easily run a discovery upon a network in a single click, without entering the details of that network each and every time. Use Open-AudIT Professional and Enterprise to schedule your Discoveries to run automatically whenever you like.
Open-AudIT can tell you what changed, what was added or removed and when it occurred. Open-AudIT has a powerful change detection engine. Any device attributes that are added, removed or changed will be detected and stored. These changes can be reported upon and the relevant data confirmed as to what was expected from your company change and release process.
Record the details of your software licenses and asset warranties with Open-AudIT and report on them as easily as ever.
Software Licenses and warranties are an essential item to track. Open-AudIT makes it easy to record and report on warranties. Easily create reports to tell you what devices have expiring warranties or licenses and have them run automatically. Be able to forecast your replacement equipment purchases for your next purchase period simply and easily.
Once Open-AudIT is setup, you can sit back and relax. Have change reports emailed to you on a schedule, for example – what new devices did we discover this week? What new software was installed this week? Were there any hardware changes last month?
Expand on the stored fields easily with your own custom attributes.
Even add devices that aren’t connected to your network or those devices your Open-AudIT server cannot reach.
Computers, switches, routers, printers or any other device on your network – Open-AudIT can audit them all.
System Integration with Open-AudIT is extensible with custom fields. If you have a particular attribute you need to record, easily add it to the database and use it to report or even group devices.
Open-AudIT can store information in custom fields that are associated with each device.
Once a Field has been created it can be used in queries and groups just like any other attribute in the database.
Open-AudIT comes with many queries inbuilt. If you require a specific query and none of the pre-packaged queries fit your needs, it’s quite easy to create a new one and load it into Open-AudIT for running.
Join Mark Henry in this webinar as he discusses how to create your own custom queries.
Open-AudIT Professional and Enterprise include fast and easy exporting of detailed device-level information in multiple formats.
Quickly and easily select which device details you want to view and export. Select your format; screen or CSV file, and the level of data you want.
Open-AudIT Enterprise includes User Roles, full role-based access control (RBAC) allowing fine-grained control over each user’s experience.
Get the complete Open-AudIT Enterprise experience. Creating roles allows fine-grained control over what your users can do within Open-AudIT.
The primary method for authorisation (what a user can do) is based on the user’s Roles. Default roles are defined as admin, org_admin, reporter and user. Each role has a set of permissions (Create, Read, Update, Delete) for each endpoint. The ability to define additional roles and edit existing roles is enabled in Open-AudIT Enterprise.
Roles can also be used with LDAP (Active Directory and OpenLDAP) authorisation. Enterprise licensed installations have the ability to customize the LDAP group for each defined role.
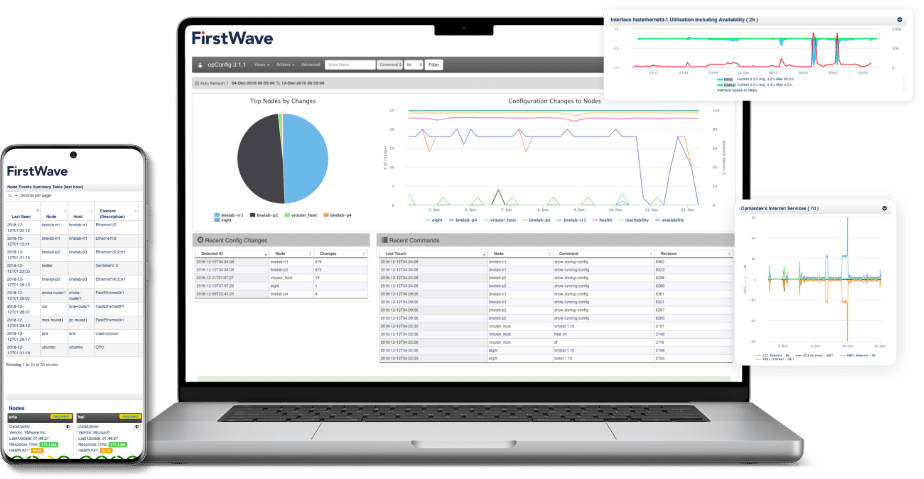
Open-AudIT Professional and Enterprises’ interactive Dashboard provides a single point of access to audit status and results. Simple, intuitive, dynamic – just some of the words used to describe Open-AudIT Enterprises’ interactive dashboard.
Professional users have the ability to choose between two dashboards that provide a single point of access to audit status, new software installs, device breakdowns, and fast access to missing devices.
Enterprise users get five dashboards shipped and also have the ability to create, update and delete widgets, giving them full customization over their dashboard.
Open-AudIT Professional and Enterprise leverage Google Maps to provide live, interactive geographic mapping of device location.
Open-AudIT Professional and Enterprise leverage Google Maps to provide live, interactive geographic mapping of device location. Automated conversion of street addresses to geocodes and long/lat along with assignment of devices to locations during discovery make mapping easy and intuitive.
Open-AudIT Professional and Enterprise include Enhanced Reporting features, including time-based, historical, and muti-query based reporting features in multiple formats.
Open-AudIT Professional and Enterprise make report creation effortless through Enhanced Reporting features like time-based reports, historical reports, and multi-query based reporting. Reports can be created dynamically and interacted with on screen, or exported to CVS for further analysis.
Simply Select which types of devices you want to be exported, which queries to run, and the format you want. Export to CSV and analyze offline, or import into your favorite third party data visualizer. The power is in your hands with Open-AudIT Enterprise Enhanced Reporting.
Network Automation has never been easier. Open-AudIT Professional and Enterprise include Task Scheduling. Schedule device discovery, report generation, or run a baseline check on any schedule you need, as often as you need, or run them on-demand from one interface.
Open-AudIT can send you a report, run a discovery or test a baseline on a schedule of your choosing. Have Open-AudIT email you a report of any new devices found for the week, every Friday. Simple, quick and easy.
When a discovery is run, the relevant discovery scan option is chosen and those settings are used by Nmap to scan the target devices. If no option set is chosen, the default configuration item (discovery_default_scan_option) is selected and used.
If a device is individually discovered using the “Discover Device” link on the device details page, we first check if this device has been discovered previously (by Discovery) and if so, use the discovery options from that scan. If it has not been previously discovered, we revert to the configuration item discovery_default_scan_option the settings.
With the 3.3.0 release of Open-AudIT we have introduced the concept of a Cluster. This intuitively maps to the idea of a web, database, file (or one of several other purposes) cluster in a given type (high availability, redundancy, scaling, etc).
Depending on the purpose of the cluster chosen, the reporting will be slightly different.
For example, if you create a Cluster with a purpose of virtualisation, when you have added devices to it you will also see the virtual machines on those devices. An example is below.
Clusters are just another collection, like any other. An entry for them in Roles-Permissions has been created. You can Create, Read, Update and Delete them using the API like any other collection.
In the future we hope to be able to automatically detect Microsoft SQL and File clusters along with ESXi clusters.
With the release of Open-AudIT 3.2.0 we have introduced a new concept called Rules. Rules are created and run against a device when the device is discovered or an audit result is processed. Rules can be used to set a device attribute based on other attributes.
Each time a device is discovered or an audit result is processed, all rules are retrieved from the database and run against the attributes of the specific device. Rules run against one device at a time – there is no facility to say “Run the rules against all devices” or “Run the rules against these devices”. An individual rule will test one or more attributes of the device and if they match the rule, the result will be applied. Several attributes can be tested. Several attributes can be set. Think of this as an If This, Then That system for Open-AudIT.
Amazing support from FirstWave – or the community if you like. It’s the no excuses, no exceptions, can-do way of thinking that our staff bring to work every day. Your complete satisfaction is our priority. Anything less is simply unacceptable.
Open-AudIT is supported by FirstWave with an amazing level of support. If you prefer an active community of support givers, there’s that as well. Where else can you talk directly to the developers and get a response within 24 hours? Just try that with other products! Amazing support. Full stop. You need support, we provide support. No if’s or but’s. Great support. Period.
The Integrations endpoint allows you to define an integration which you can then use to import and export Open-AudIT data to an external system. At present the single supported Integration type is “nmis”.
This is as it was prior to 4.2.0. With 4.2.0 an onward we have rewritten the code from the ground up to work in an external system agnostic way. With the 4.2.0 release we ship with a default Integration already created for NMIS. Going forward other external systems will be supported. All that is required is a new file to implement the required functions that an integration needs. There are no external dependencies or prerequisites.
For the purpose or brevity, you can substitute any external system where I refer to NMIS below (when implemented).
Our goal with the release of the initial integration was specifically for NMIS to Open-AudIT integration to “just work”. If you are using the programs on Linux, you can literally click a single button to execute the integration. Nothing more is required. Having said that, the integration itself is extremely configurable – so if something isn’t to your preference, it can easily be changed.
If you are using Open-AudIT on Windows or if your NMIS server isn’t on your Open-AudIT Server (in the case of some Linux installs), you will need to supply access credentials and a URL to the remote NMIS – but that’s all! Yes – Integrations between NMIS and Open-AudIT even work with Windows-based Open-AudIT now!
A rack is a collection of devices which are assigned a position and height within the rack. A device can optionally have a picture associated with it, from the supplied set or custom to your environment.
We have created a very granular system for positioning of racks, which is as follows. At the top level (as always) is the Organization (Org). An Org can have multiple locations (as has always been the case). With the addition of the Racks feature, a location can now contain one or more Buildings. A building has one or more Floors. A floor has one or more Rooms. A room has one or more Rows.
Create a new Location and the sub-components will be automatically created for you. If you need more items (buildings, rooms, etc.), you can add them as you need. A rack can also be part of a “pod” of racks. The pod attribute works as a tag, rather than a strict hierarchical inheritance model as per buildings, floors, etc.
Racks are a feature available to Open-AudIT Enterprise licensed customers.
With the introduction of the Clouds feature, you can supply details of your cloud, Amazon AWS or Microsoft Azure, and Open-AudIT will use the relevant API to retrieve a list of locations, networks, and instances, then discover each of these instances.
Full cloud auditing with all the details from a regular Open-AudIT audit and details such as the machine type and size.
Once you have your cloud credentials, it is merely a matter of creating a new cloud and running the discovery – or scheduling first/future discoveries. Make sure you also have the credentials required to log on to your cloud machines, and it is all done for you just like a regular discovery.
Clouds are a feature available to Open-AudIT Enterprise licensed customers.
Open-AudIT Enterprise includes Files, providing change control monitoring of individual files and folders on both Linux and Windows servers.
Get the complete Open-AudIT Enterprise experience. Audit your computers and ensure any changed files are recorded. Open-AudIT can retrieve details about a file or directory of files and monitor these files for changes as per other attributes in the Open-AudIT database.
Details such as name, directory, size, hash, last changed and permissions are all recorded. This feature works on both Windows and Linux target machines.
This is ideal for monitoring configuration files in /etc on Linux machines (for example).
Open-AudIT Enterprise includes Baselines, a light-weight compliance system that compares software, users, and netstat data against your required standard.
Get the complete Open-AudIT Enterprise experience. Track your devices and see if they deviate from your required standard.
Baselines enable you to combine audit data with a set of attributes you have previously defined (your baseline) to determine compliance of devices.
For example – you might create a baseline from a device running Centos 6 which acts as one of your Apache servers in a cluster. You know this particular server is configured just the way you want it but you’re unsure if other servers in the cluster are configured exactly the same. Baselines enable you to determine this.
You can create a baseline, run it against a group of devices and view the results. You can implement your baselines to be executed on a schedule. All results are kept and can be viewed and exported.
Open-AudIT Cloud and Open-AudIT Enterprise both work standalone and with collectors. You should use a collector for any difficult to reach devices that you need to audit or in cases where your security only allows port 80 or 443 to be used to access a network. Both products come with 1 collector free of charge.
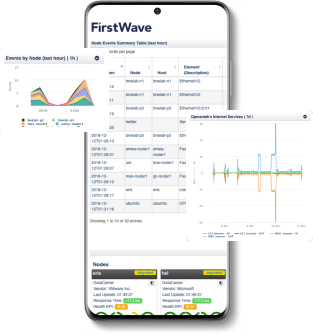
Open-AudIT Professional and Enterprises’ interactive Dashboard provides a single point of access to audit status and results. Simple, intuitive, dynamic – just some of the words used to describe Open-AudIT Enterprises’ interactive dashboard.
Professional users have the ability to choose between two dashboards that provide a single point of access to audit status, new software installs, device breakdowns, and fast access to missing devices.
Enterprise users get five dashboards shipped and also have the ability to create, update and delete widgets, giving them full customization over their dashboard.
When a discovery is run, the relevant discovery scan option is chosen and those settings used by Nmap to scan the target devices. If no option set is chosen, the default configuration item (discovery_default_scan_option) is selected and used.
If a device is individually discovered using the “Discover Device” link on the device details page, we first check if this device has been discovered previously (by Discovery) and if so, use the discovery options from that scan. If it has not been previously discovered, we revert to the configuration item discovery_default_scan_option the settings.
Open-AudIT Enterprise includes User Roles, full role-based access control (RBAC) allowing fine-grained control over each user’s experience.
Get the complete Open-AudIT Enterprise experience. Creating roles allows fine-grained control over what your users can do within Open-AudIT.
The primary method for authorisation (what a user can do) is based on the user’s Roles. Default roles are defined as admin, org_admin, reporter and user. Each role has a set of permissions (Create, Read, Update, Delete) for each endpoint. The ability to define additional roles and edit existing roles is enabled in Open-AudIT Enterprise.
Roles can also be used with LDAP (Active Directory and OpenLDAP) authorisation. Enterprise licensed installations have the ability to customize the LDAP group for each defined role.
Download Open-AudIT
Open-AudIT is a powerful network management tool used by over 130,000 organizations internationally to collect data from large and complicated networks.
Note: Windows download is not compatible with Windows 10. FirstWave use and recommend Windows Server 2016.
Get A Custom Quote
- Predictable and transparent pricing
- Pricing that scales with you
- Support is always included
FirstWave’s team can help you get a quote that meets your requirements. A 15-minute call is all it takes. This is not a sales call—it’s an opportunity for you to tell us about your organisation’s network management needs.
Setup Guide
Need Help Getting Started?
Download
Open-AudIT
Open-AudIT is a powerful network management tool used by over 130,000 organizations internationally to collect data from large and complicated networks.
Note: Windows download is not compatible with Windows 10. FirstWave use and recommend Windows Server 2016.
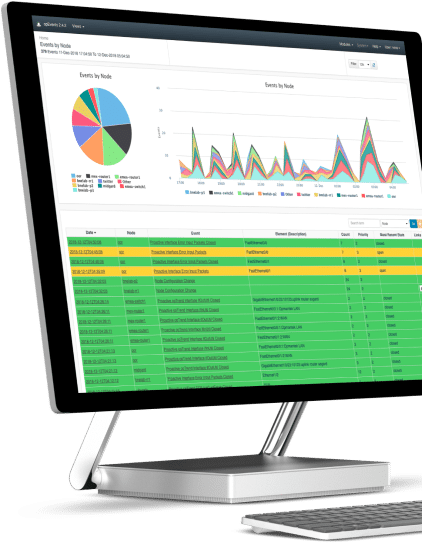
Quick Setup
Open-AudIT is one of FirstWave’s software packages available either standalone or as part of our network management suite. While this guide covers a standalone Linux installation, Open-AudIT may also be installed as part of the FirstWave Virtual Machine, which includes NMIS and all network monitoring software modules, or on Windows. You can find links to the alternative installation guides below:
The following installation guide should be sufficient for most Linux users’ needs. Advanced instructions and troubleshooting are available on the Open-AudIT Wiki.
1. Download the Open-AudIT installer
If you haven’t already, hit the download button above and download the Open-AudIT Installer. The Installer comes as a .run file.
2. Run the Installer in Linux Terminal
Open the Linux Terminal. Start a Terminal instance as the root user through the following command, entering your password when prompted: sudo -i
If you have not been granted access to the root user, contact your system administrator. Once your terminal session is run by the root user, run the shell command to begin the installation process
sh OAE-Linux-<version number>.run
Press Y or Return/Enter when the installer prompts you. Several times throughout the installation process you will be prompted to approve the various components of the Open-AudIT Module as they are installed on your machine. Please take note of any relevant information as you approve each step. When the installation is complete, the following will print on the Terminal:
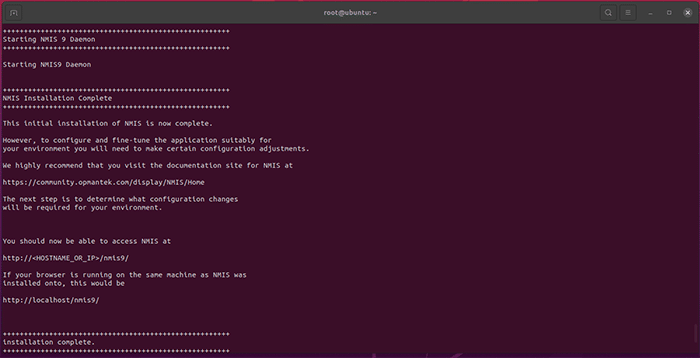
You’re now ready to license Open-AudIT.
Good news! Each of FirstWave’s network monitoring software modules offer a free time-unlimited 20-node license. The first time you open each program, you will be given the opportunity to activate a free license.
Time-limited trials are also available if you want to test the software on a larger network, and licenses for running FirstWave’s software modules on larger networks are available by request.
Launch Open-AudIT
Launch Open-AudIT in a browser using the address provided by the installer. If you’re accessing the software on the same machine the address will be localhost/omk/open-audit. If you are using a different machine, use <IP_OR_hostname>/omk/open-audit to connect. You can find your host machine’s IP address in Network Settings.
Open-AudIT
Open-AudIT allows you to discover devices and to take inventory of who and what is connected to your network. When you open the software, you should be greeted by the landing page below.
Explore FirstWave’s extensive software documentation
You’re now ready to configure Open-AudIT to exactly your needs and to begin discovering devices on your network using the guides on the FirstWave Wiki. In no time at all, you’ll have a fuller view of your network than you’ve ever had before.
General FAQs
Do I need to provide the operating system or any databases?
That depends on you. You can install Open-AudIT on Windows, Linux, or you can choose to use our virtual machine – all set up and ready to go. There is no need for a separate database install as our installer provides that and uses MySQL which is free to use yet scales to enterprise levels.
Do you offer a free trial
Yes, Open-AudIT Professional is free for life to use on 20 devices. There is no pressure to upgrade unless you need more devices.
Does Open-AudIT discover every device?
If it is connected to your network Open-AudIT will find it.
Can I use Open-AudIT to track all my inventory?
Open-AudIT is a suite of powerful tools that will discover and audit all the devices on your network.
Is Open-AudIT only for hardware?
No, with Open-AudIT you can rest assured you know where your equipment is, what you have, and where your software licenses are being used.
Can Open-AudIT detect hardware changes?
Yes, Open-AudIT can detect all changes to hardware and software. It can even record the most recent user to a machine for security purposes.
Will I need to install software on all my devices?
No, Open-AudIT is completely agentless and doesn’t install software on any device. This makes it simple not only to start using but also to upgrade to newer versions.
Can I get custom features?
Yes, the expansive feature set we offer has come from years of networking experience and collaborations with clients. If you have a custom feature you want, we may be able to integrate it. Contact our engineers to see if it is feasible.
Can I keep my existing software?
Yes, Open-AudIT will work alongside any software, you can keep everything on your system as is.
Can I use Open-AudIT for compliance testing?
With Open-AudIT Enterprise’s Baselines anyone can quickly and easily create compliance rules and ensure their servers and workstations are configured properly.
What is an Open-AudIT Collector?
A collector is Open-AudIT set to collector mode, where its sole purpose is to collect asset information. While the collector is capable of discovering multiple networks, it is perfect for running discoveries on its own subnet.
How does an OpenAudIT Collector work?
When in Collector / Server configuration you can have a collector Open-AudIT running on a subnet and discovering devices where the collector is controlled by the server. Once installed and setup, control of the collector is performed on the server. The only required network ports between the collector and server are 80 or 443.
When will I need to use an OpenAudIT Collector?
When you have segregated networks that you need to audit. It saves firewall changes as it uses ports 80 or 443 and shouldn’t cause any concern for the security team. There is no requirement for the Open-AudIT server to have full access to the network on which the collector runs.
How can I figure out how many OpenAudIT collectors I need?
You should consider what you want to audit, the frequency of audits and how many nodes you want to audit and use that as a starting point to determine the number you need (if any). You can:
- Have one collector per subnet
- One collector per many subnets
- One collector behind a firewall (via port 80 or 443)
Ready To Take the Next Step with Open-AudIT?
Book In For A Guided Demonstration
Book in your custom demo with one of our software specialists to see the power of our network solutions in action. All demonstrations are interactive, personalized, and free.

For Further Information
FirstWave Head Office
FirstWave Technical Support
Support Email
FirstWave Sales Support
Sales Email
Need Help?
Find out how FirstWave can scale your network
management and cybersecurity of your business?

